Cyber Security Protection
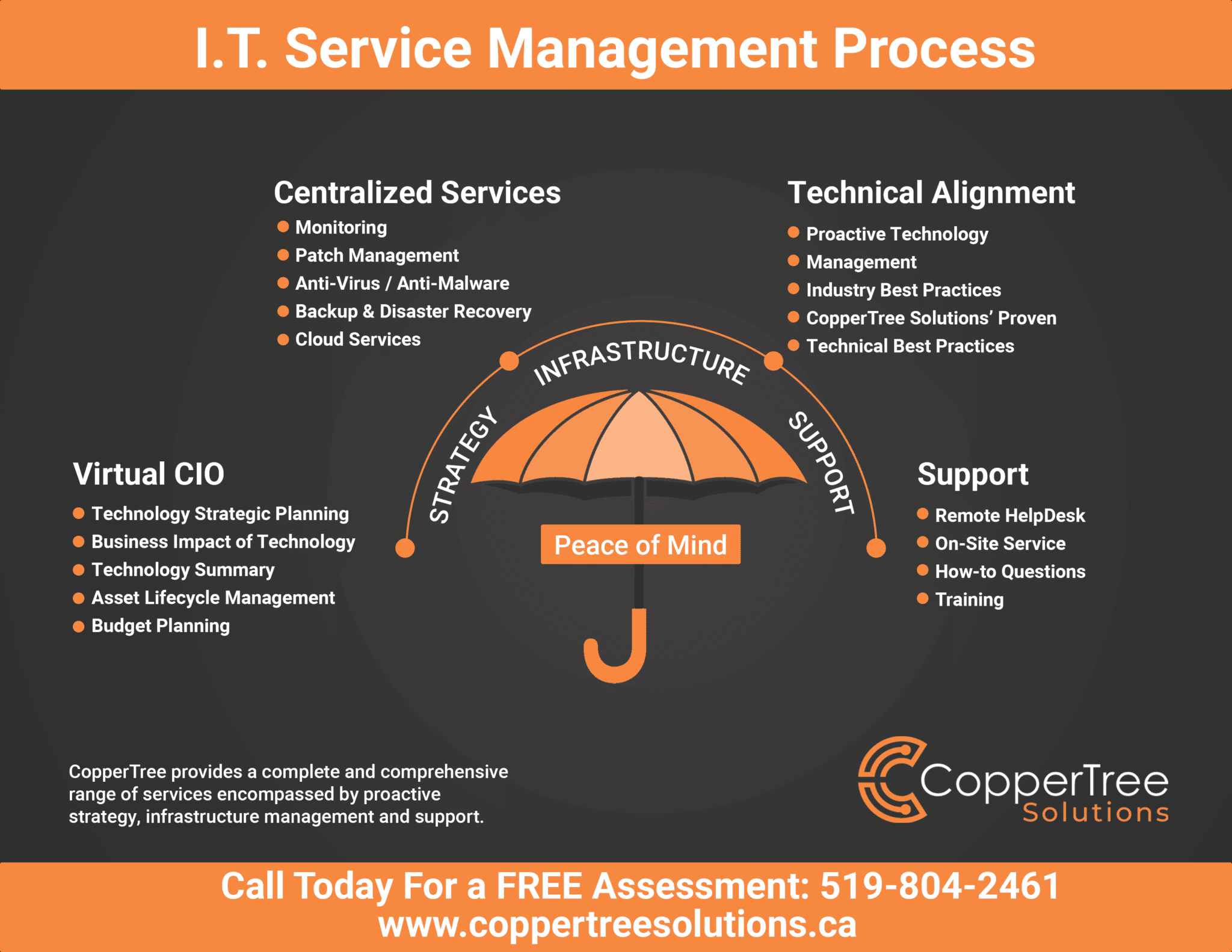
THE I.T. SERVICE MANAGEMENT PROCESS
CopperTree’s managed I.T. services include around-the-clock monitoring and management of intrusion detection, firewall installation, and the overseeing of patch management and upgrades. We protect your data from malware and ransomware, help you to define and implement cybersecurity policies, and perform regular security assessments and audits. If the need arises for emergency IT support, we respond quickly with timely resolution. A proactive team approach to I.T. will save you time & money because when a breach does happen we are ready for it.
OUR HAPPY AND PROTECTED CLIENTS
THIS IS HOW WE PROTECT YOU FROM CYBERCRIMINALS

Avoid, identify, and eliminate threats. As part of our managed I.T. support service we assess your email system and implement tools for spam filtering and anti-phishing, spyware/malware protection, encryption, and password management.

Proactive monitoring. We continually monitor your endpoints and infrastructure, 24 x 7 x 365 to detect signs of vulnerability, such as penetration attempts, malicious footholds, and security breaches. If a threat is uncovered, we Isolate the system and implement remediation.

Correct Authorization. We help you to be sure that the person logging into the network is who they say they are. CopperTree will set up multi-factor authentication to verify identities, and then manage access to your data based on the user’s “need to use.”

Identify problems before they happen. Through regular assessments, we evaluate the security of your entire network, and update your configurations to make sure your network is secure and reliable. Our approach is designed to implement best practices in order to assure proper configuration over time.

Define standard operating procedures. Security is about more than just the technology. If a ransomware attack or I.T. incident occurs, the speed and consistency of your response team makes all the difference. We work with you to create a written policy, test it regularly, and train your staff on how to respond in the event of an incident.

Regularly assess and close gaps. Our Managed I.T. support process regularly assesses your entire I.T. infrastructure to meet best practices. We’ll put the most advanced technologies and tools into place and make sure they are current to protect against threat actors.
NOT SO FUN FACTS ABOUT CYBERATTACKS

22 DAYS
FOR A COMPANY TO RECOVER FROM A CYBERATTACK

78%
COMPANIES GET BREACHED AT LEAST ONCE WITHIN A 12-MONTH PERIOD

$6.35M
AVERAGE COST OF BREACH FOR CANADIAN COMPANIES
STATISTICS FROM THE GOVERNMENT OF CANADA*
ARE YOU PREPARED FOR WHEN THIS HAPPENS TO YOU?

BACKUP RECOVERY

EMERGENCY & DISASTER PLAN

PROACTIVE APPROACH TO I.T.
LET’S TAKE ACTION!
It’s time to think about your business growth. Book a free meeting with our experts. Stop worrying about your I.T. security and focus on growth while leaving I.T. to us.




